China captured a spy tool deployed by the US National Security Agency, which is capable of lurking in a victim's computer to access sensitive information and was found to have controlled global internet equipment and stole large amounts of users' information, according to a report the Global Times obtained from the National Computer Virus Emergency Response Center exclusively on Monday.
`
According to the report, the Trojan horse, "NOPEN," is a remote control tool for Unix/Linux computer systems. It is mainly used for stealing files, accessing systems, redirecting network communication, and viewing a target device's information.
`
Through technical analysis, the center believes that the "NOPEN" Trojan horse is characterized by complex technology, comprehensive functions and strong concealment, which can fit a variety of processor architectures and operating systems. It can also collaborate with other cyber weapons and is a typical tool used for cyber espionage.
`
The report came after the NSA was exposed to have been launching cyberattacks against 47 countries and regions for a decade, with Chinese government departments, high-tech companies and military-related institutes among the key targets. Under the surveillance of the NSA, the privacy and sensitive information of hundreds of millions of people around the world were exposed, like "running around naked."
`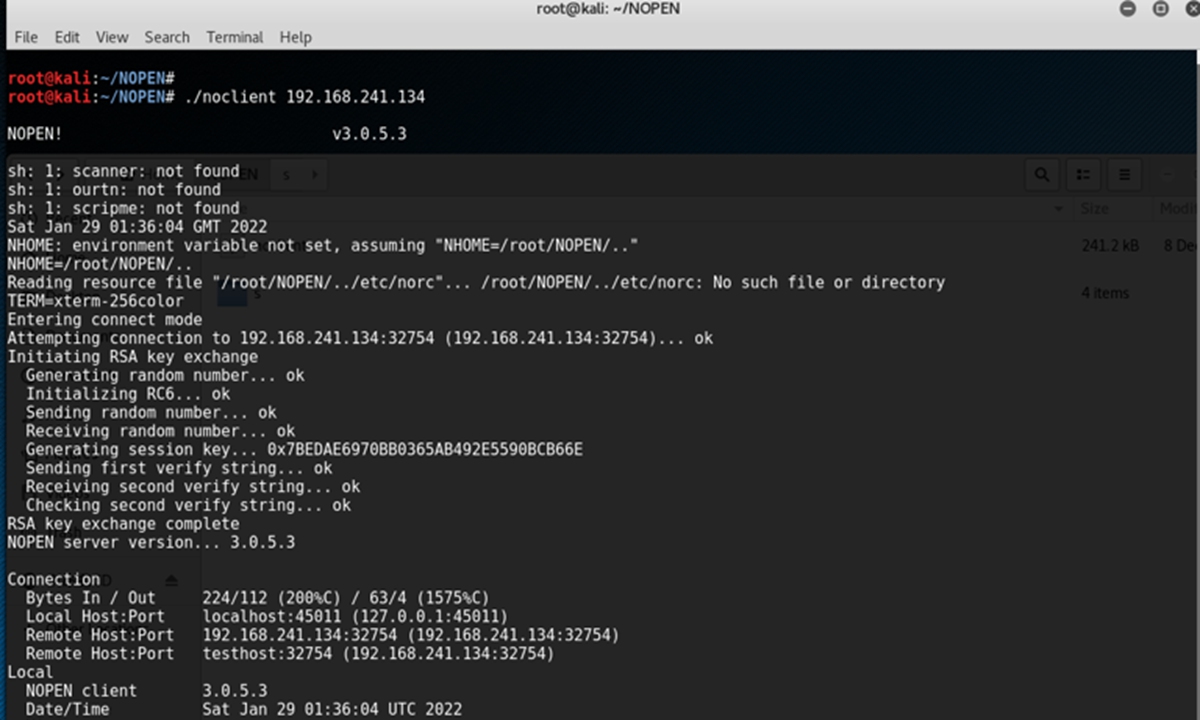
Photo: Courtesy of National Computer Virus Emergency Response Center
`
Cybersecurity experts told the Global Times that once the Trojan was planted into a victim's computer, it would become a "lurker" waiting for the "code" and opening the "vault door" for hackers. The Trojan also could turn a victim's computer into a bridge tower, allowing hackers to go deeper into the group where the victim works and grasp the company's information.
`
According to the center's report, the "NOPEN" can remotely control most existing network servers and terminals, which can be manually implanted by attackers, or cyberattack platforms by the NSA. It can execute a variety of instructions such as information theft and destruction.
`
Evidence shows that the NSA used the "NOPEN" Trojan horse to control a large number of internet devices around the world and steal user privacy data, which has caused inestimable losses.
`
According to internal NSA documents leaked by hacking group Shadow Brokers, "NOPEN" is one of the powerful weapons used by the NSA's Tailored Access Operations (TAO) to attack and steal secrets.
`
"As the research and development arm of the world's top military power, the NSA cannot develop weapons that rust in their arsenals," a Chinese cybersecurity expert told the Global Times on condition of anonymity. "The international community has learned from the PRISM scandal that the US military intelligence agency has been conducting network monitoring and cybertheft of countries around the world for a long time, and these cyber weapons are an important means of its implementation of network monitoring."
`
In April 2017, the Shadow Brokers released a large number of cyberattack tools developed by the NSA. As the NSA is affiliated with the US Department of Defense, the tools are widely believed to be used for military purposes as "cyber weapons."
`
For example, on May 12, 2017, the worldwide WannaCry ransomware used EternalBlue, a computer exploit developed by the NSA to attack unpatched computers, which brought serious damage and data loss to many enterprises and individuals, according to media reports. The incident enabled the international community to witness for the first time the terrible power of cyber weapons, but such weapons of mass destruction are only the tip of the iceberg in the NSA's vast arsenal.
`
"The vast majority of the NSA's arsenal consists of stealth fighters and submarines that can easily attack victims without theirknowledge," the anonymous expert said, noting that the "NOPEN" Trojan horse is the main weapon of the NSA's arsenal.
`
The expert said the center's report sounds an alarm to the world as there are likely a large number of undetected victims online, who face long-term and serious cybersecurity risks. The leakage and proliferation of these cyber weapons further aggravate the increasingly severe network security situation, seriously endanger the overall security of the cyberspace, turning military confrontation in cyberspace into a "zero-sum" game.
Chinese cybersecurity experts for the first time disclosed a typical weapon used by US National Security Agency (NSA) to target ...
China's top diplomat Yang Jiechi met with US National Security Advisor Jake Sullivan in the Italian capital of Rome on ..







No comments:
Post a Comment